

In today’s fast-paced complex digital environment, business leaders often worry if their security controls are effective enough to defend against persistent cyber threats. Questions such as “Are our security controls effective?”, and “Do we have the right tools deployed?” can keep any business leader up at night.
The best way to address these concerns is by building a cybersecurity strategy with compliance as its core foundation. Compliance in cybersecurity is not just about meeting legal requirements; it’s a critical strategy that protects organizations and bolsters their security posture against potential breaches. However, the relationship between compliance and regulatory requirements can be complicated and confusing. We will explore further the differences between the two and help you determine the level of compliance you should be incorporating into your cybersecurity strategy.
Regulations: legal requirements and standards set by government or authoritative bodies to ensure safety and order.
Purpose: To establish legal requirements for certain industries to ensure safety, fairness and order.
Scope: Broad and applies to entire sectors or activities, specifying what must be done to comply with the law.
Enforceable: They are enforced through inspections, penalties, and legal actions if the rules are violated.
Compliance: An execution strategy implemented by an organization that results in adhering to a set of standards. These standards can be:
Purpose: Ensure the organization meets these standards, whether internally developed or externally imposed.
Scope: compliance is specific to the organization and can look different across different industries
Implementation: Tailored strategies, policies, and practices to meet the relevant standards. Examples of some specific activities may involve:
Origin: Regulations are set by external bodies while compliance is implemented internally.
Focus: Regulations focus on what needs to be achieved, compliance focuses on how to achieve it.
Enforcement vs. Implementation: Regulations are enforced by the authorities; compliance is internally managed.
By ensuring that your security controls and functions adhere to industry best practices and standards, you establish a structured approach to cybersecurity that can identify weaknesses in your defences.
Aligning your organization security frameworks to standards like NIST, CIS, ISO 27001, GDPR, and SOC 2 is crucial for uncovering vulnerabilities, mitigating risks, and enhancing your overall security posture. Depending on your industry, some of these standards are legally required.
While most of these frameworks offer a compliance certification, pursuing certification is optional. However, achieving certification represents the gold standard for a strong security strategy. Alternatively, adapting your internal standards to align with the relevant requirements within these frameworks can be a way to strengthen your strategy.
If you’ve determined that your internal strategy doesn’t need to be certified, you should ensure compliance to consumer data and privacy regulations. Building controls and policies around requirements such as GDPR and PIPEDA, is a proactive approach to compliance. Positioning yourself ahead of compliance can provide a competitive advantage, especially in industries where data security is a critical component of the business operation.
In today’s market, consumer trust is paramount. Customers are more likely to engage with businesses they believe are secure and responsible with their data. Compliance with recognized security standards reassures customers, stakeholders, and partners that an organization is serious about protecting sensitive information. This is not just beneficial for customer retention but also attracts new business by demonstrating a commitment to security.
Embedding compliance into cybersecurity strategies encourages a proactive instead of a reactive approach to security. Regular audits, continuous monitoring, and updates to security practices ensures that security measures are always up to date and effective against current cyber threats.
The first step in identifying the strength of your cybersecurity strategy is to assess your current level of compliance. Consider the following descriptions to understand your current compliance stage and identify your target compliance strategy:
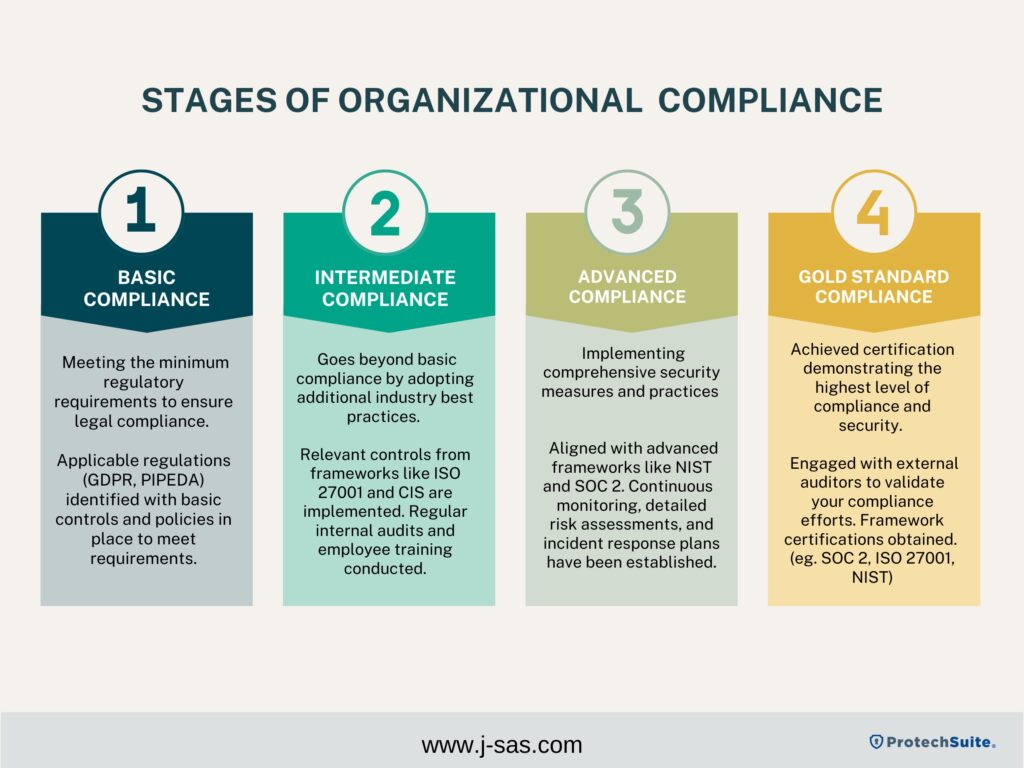
Stage 1 – Basic Compliance: Meeting the minimum regulatory requirements to ensure legal compliance.
Current Actions: Applicable regulation (e.g., GDPR, PIPEDA) have been identified. Basic controls and policies are in place to meet these standards.
Stage 2 – Intermediate Compliance: Goes beyond basic compliance by adopting additional industry best practices to enhance data protection.
Current Actions: Relevant controls from security frameworks like ISO 27001 and CIS have been implemented. Regular internal audits and employee training are conducted.
Stage 3 – Advanced Compliance: Implementing comprehensive security measures and practices to ensure robust protection and compliance.
Current Actions: Aligned with advanced frameworks like NIST and SOC 2. Continuous monitoring, detailed risk assessments, and incident response plans have been established.
Stage 4 – Gold Standard Compliance: Achieving certification in recognized frameworks to demonstrate the highest level of compliance and security.
Current Actions: Engaged with external auditors to validate your compliance efforts from stage 2 and 3. Obtain certifications for frameworks such as SOC 2, ISO 27001, and NIST
Understanding your current stage in the compliance process will make it easier to integrate compliance into your strategy.
Develop a Compliance Plan: Create a plan to address gaps with timelines, resources, and responsibilities.
ProtechSuite can streamline your compliance and cyber security efforts. Our solution automates every step, saving you time and resources that can be better used to drive your business forward. Don’t let compliance slow you down. Reach out for a demo or free trial to see how it works: Book a Demo







